Ransomware Attacks, Definition, Examples, Protection, Removal
Ransomware has become a serious threat to the online globe these days. Many software firms, universities, companies, and organizations effectually the world are trying to have precautionary measures to save themselves from ransomware attacks. The United states and Canadian governments have issued a joint statement virtually ransomware attacks urging users to stay alert and have precautions. Recently on May xixthursday, the Swiss regime observed the Ransomware Info Solar day, to spread sensation regarding ransomware and its effects. Ransomware in India too is on the rise.
Microsoft recently published a data mentioning how many machines (users) were affected past ransomware attacks beyond the world. It was establish that the U.s.a. was on the tiptop of ransomware attacks; followed past Italy and Canada. Here are the top 20 countries which are majorly affected past ransomware attacks.
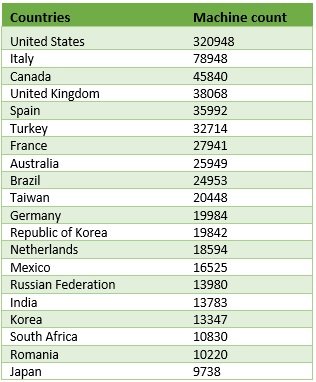
Here is a detailed write-up that volition answer about of your questions regarding ransomware. This post will accept a look at What are Ransomware Attacks, the Types of ransomware, How does ransomware gets on your computer and suggests means of dealing with ransomware.
Ransomware attacks
What is Ransomware
Ransomware is a type of malware that locks your files, information or the PC itself and extorts money from you in social club to provide access. This is a new way for malware writers to 'collect funds' for their illegitimate activities on the web.
How does ransomware become on your computer
You could get ransomware if you click on a bad link or open a malicious e-mail zipper. This paradigm from Microsoft describes how the ransomware infection takes place.
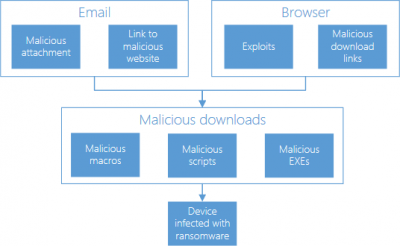
Ransomware looks similar an innocent programme or a plugin or an e-mail with a 'clean' looking attachment that gets installed without the user's knowledge. As before long as it gets its access to the user'due south system, information technology starts spreading across the system. Finally, at one point of time, the ransomware locks the system or item files and restricts the user from accessing information technology. Sometimes, these files are encrypted. A ransomware writer demands a certain corporeality of coin to provide access or decrypt the files.
A imitation warning message by a ransomware looks equally follows:
Yet, during the ransomware attacks, there is no guarantee that the users will get back their files even after paying the ransom. Hence, information technology is ameliorate to prevent ransomware attacks than trying to get dorsum your data from some mode or another. You may use RanSim Ransomware Simulator to bank check if your computer is sufficiently protected.
Read: What to do after a Ransomware set on on your Windows estimator?
How to identify ransomware attacks
The ransomware generally attacks the personal data, such every bit user's pictures, documents, files, and data. It is easy to place the ransomware. If you see a ransomware notation demanding money to requite access to your files, or encrypted files, renamed files, locked browser or a locked screen of your PC, you can say that ransomware has got a grip on your organization.
However, the symptoms of ransomware attacks tin can alter equally per the types of ransomware.
Read: Malware Tracker Maps that let you view Cyber Attacks in real-time.
Types of ransomware attacks
Before, ransomware used to display a message stating that the user has washed something illegal and they are being fined by the police or the government agency on the basis of some policy. To go rid of these 'charges' (which were definitely false charges), users were asked to pay these fines.
Nowadays, a ransomware attack in ii ways. It either locks the computer screen or encrypts certain files with a password. Based on these 2 types, the ransomware is divided into ii types:
- Lock screen ransomware
- Encryption ransomware.
Lock screen ransomware locks your organisation and demands a ransom for letting yous access it once again. The second type, i.e. the Encryption ransomware, changes the files in your system and demands money to decrypt them again.
The other types of ransomware are:
- Master Kick Record (MBR) ransomware
- Ransomware encrypting web servers
- Android mobile device ransomware
- IoT ransomware.
Here are some ransomware families and their statistics of attacks:

Too, take a await at the Ransomware growth and its infection statistics.
Who can be afflicted past the ransomware attacks
Information technology doesn't matter where you are and what device you are using. Ransomware tin assault anybody, someday and anywhere. The ransomware attacks tin can take place on whatever mobile device, PC or laptop when y'all are using the cyberspace for surfing, emailing, working, or shopping online. Once it finds a mode to your mobile device or the PC, it will employ its encryption and monetization strategies into that PC and mobile device.
When tin can ransomware become a chance to attack
So what are the possible events when ransomware can strike?
- If you lot are browsing untrusted websites
- Downloading or opening file attachments received from unknown electronic mail senders (spam emails). Some of the file extensions of these attachments can exist, (.ade, .adp, .ani, .bas, .bat, .chm, .cmd, .com, .cpl, .crt, .hlp, .ht, .hta, .inf, .ins, .isp, .job, .js, .jse, .lnk, .mda, .mdb, .mde, .mdz, .msc, .msi, .msp, .mst, .pcd, .reg, .scr, .sct, .shs, .url, .vb, .vbe, .vbs, .wsc, .wsf, .wsh, .exe, .pif.) And also he file types that back up macros (.dr., .xls, .docm, .xlsm, .pptm, etc.)
- Installing pirated software, outdated software programs or operating systems
- Logging into a PC that is a part of the already infected network
Precautions confronting ransomware attacks
The only reason ransomware is created, is because the malware writers run across it equally an piece of cake fashion to make money. Vulnerabilities such as unpatched software, outdated operating systems or people's ignorance is beneficial for such people with malicious and criminal intentions. Hence, awareness is the best style to avoid whatever attacks by ransomware.
Here are are a few steps you lot tin can have to tackle or deal with ransomware attacks:
- Windows users brash keeping their Windows Operating System upward-to-appointment. If y'all upgrade to Windows 10, y'all will reduce the events of the ransomware attack to the maximum extent.
- E'er dorsum-upwards your important information in an external difficult-drive.
- Enable file history or system protection.
- Beware of phishing emails, spam, and check the email earlier clicking the malicious attachment.
- Disable the loading of macros in your Function programs.
- Disable your Remote Desktop characteristic whenever possible.
- Utilize two-gene authentication.
- Use a safe and password-protected internet connection.
- Avoid browsing websites that are often the convenance grounds for malware such every bit illegal download sites, adult sites and gambling sites.
- Install, apply, and regularly update an antivirus solution
- Brand employ of some good anti-ransomware software
- Take your MongoDB security seriously to prevent your database from being hijacked past ransomware.
The Ransomware Tracker helps y'all track, mitigate and protect yourself from malware.
Read: Protect against and preclude Ransomware attacks.
While in that location are some ransomware decryptor tools available, information technology is advisable that y'all take the problem of ransomware attacks seriously. It not only endangers your information, merely information technology tin also breach your privacy to such extent that it can damage your reputation also.
Says Microsoft,
The number of enterprise victims existence targeted by ransomware is increasing. The sensitive files are encrypted, and large amounts of money are demanded to restore the files. Due to the encryption of the files, it tin be practically incommunicable to reverse-engineer the encryption or "fissure" the files without the original encryption cardinal – which simply the attackers will accept access to. The best advice for prevention is to ensure confidential, sensitive, or important files are securely backed upwardly in a remote, unconnected backup or storage facility.
If you do happen to have the misfortune of existence infected with ransomware, y'all tin can if y'all wish, report Ransomware to FBI, Constabulary or appropriate authorities.
At present read about Ransomware protection in Windows.

Source: https://www.thewindowsclub.com/ransomware-attacks-definition-faq
Posted by: hillsidia1949.blogspot.com


0 Response to "Ransomware Attacks, Definition, Examples, Protection, Removal"
Post a Comment